"It was you, listen up, tomorrow afternoon I'm going to lock in your family! "Hear this word, what would you think of that?
In front of the HackPwn Carnival geek, hacker to send a message: to be cracked on its smart car in the party. This is not naked and humiliated you? This is not a provocation and threats? This can be tolerated, whether or not? BYD team courage, after careful discussion, decision. ... Temporarily shutting down the server was holed up.

I let you watch the car to feed
HackPwn in the case "to subdue the enemy without fighting soldiers" opened in the atmosphere. In the party scene, a before and after opening the cover at any time by tapping the BYD is ready, but because the "server upgrades" cannot be networked. However, this yadi sister hacker remote start blushing like a few days ago had been recorded down, starlets, caught red handed.

Video display remote control process BYD
Yes, HackPwn is the road show hackers attack Carnival event. By the way, Pwn means to "bang", is compromised of onomatopoeic words at the moment. The party was "pop" just BYD company, from bracelets, cell phones, soya-bean milk machine, TV, washing machine, covering almost all areas of intelligent home. Are born of intelligent home appliances before the hacker full rout. Let us take a look at what the company was public "shaming" of it.
Millet bracelet abused dog
What is Chinese Valentine's day, didn't go out at night, only the right hand moves up and down regularly? HA HA HA, single dog, your bracelet has betrayed you!
This is sky vulnerability platform show Lin Wei, head of "millet bracelet child abuse a dog new tricks".
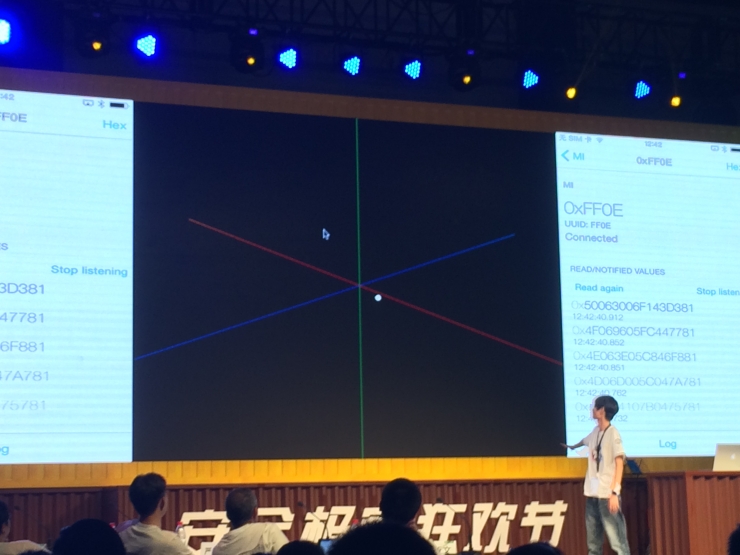
Wei Lin at the scene showed wrist motion capture figure small dots to hand real time location
Usually millet bracelet and phones paired, ring a touch hand action is needed, but in the hands of Wei Lin, millet around the validation process. So any one around his millet bracelet, all Bluetooth capture, and hackers can record all the information within the millet bracelet. Include information about your step count, sleep, and even the precise trajectory of the hand.
According to demos, even wearing a tiny shake of the hand can be recorded, as long as the basic behavior models and compare what you've done, are doing what we are there.
Lin Wei took out unopened millet bracelet, you can control its hard shaking of the box, really worried that one day he can exploit the transfer object will vibrate at the same time within a square kilometer seismic technology.
In addition, due to the millet bracelet you can unlock the phone, payment, exploiting this vulnerability could in theory do not just snooping on your personal activities as simple as well.

Bypass control lowercase uppercase easily
Minutes playing with your washing machine
TCL is the home "built death" of another enterprise. According to the hacker introduction, as a result of a live breaking news will be, HackPwn the previous day, TCL has closed cloud servers, hacking children's shoes to consumers after begging for the whole night, came back to service, but closed again today and closed the ...
TCL washing machines in the cloud to find each other. But normally, a washing machine is unable to give another command under the washing machine. However, hacker team found an enemy trick, that is: prohibit sending command characters lowercase letters, lowercase letters, lowercase. (Important things three times)

After receiving instructions of hard racing TCL washing machine
Yes, bypassing the system control is as simple as that. By using this method you can imitate clouds controller "Jingdong micro-link" to any washing instructions, instructions can be precisely to temperature and speed.
So, when you go home and find the washing machine has been set at a 90-degree temperature, with 1200 rpm speed the day when, Oh, please don't be surprised, your washing machine is just "renzeizuofu".
Are you watching TV? TV is watching you!
University of posts and telecommunications information security team to choose the CHANGHONG TV on child abuse.
This Rainbow carrying Android smart TV. However, when the team when the USB debugging check TV system which found the interface is open, and the system will also open this interface to the Internet. So the protection status, "door locked" is not enough to describe, it can be said to be "encroachments" attached note: welcome.

Is a silent install Apk CHANGHONG TV
By controlling the System Root permissions, hackers can implement software silent install, silent uninstall, no-man's. Because this TV is equipped with, were not equipped with cameras. Otherwise, the hackers take the camera permission is the easy thing. At that time, you think you're watching TV, in fact, TV is watching you. Sure TV content than you can see wonderful.
Baby goat more boring to see the ring!
Le Xiaobao is a music video produced by smart parent product, projection can be played for children pictures, telling stories, or remotely and children a voice conversation. Take off your imagination, to see if the equipment was bad control, what outcomes will be.
Beauty girls shoes love full House at Zhejiang University, decided to personally break Le Xiaobao.
By studying bought Le Xiaobao, her team found that the top six identical MAC address for each device, as long as after several exhaustive, you can find legitimate devices. Users bound only to verify, is the MAC address. So, she got one of you all of the information contained in a strange device: name, date of birth, photograph, and so on.
In addition, she considered that the device almost no possible intrusion security, greater control over Le Xiaobao is not impossible, she cited two hard usage
1, in the quiet of the night, Le Xiaobao suddenly lit up, start playing the ring "warm picture." Watched Tzu uninformed to crawl closer, and child psychological shadow area is much larger.
2, when children are alone at home, bad sound device to imitate mother's voice, tell the child: "MOM home soon, to open the door to my mother. "
A warm parent-child devices with such a bloody game. Flowers of the motherland will be cultivated as a fighting nation, duly completed.
Smart Crow's story seems to be entering into a strange thing
Heijin goddess of soya-bean milk machine
Nani? Don't even let soya-bean milk machine?
Do such a cruel thing, is the beauty of Huang Yuan 360 team to get this beauty contact details please go to black 360 security laboratory. Good luck.

As to what her black soya-bean milk machine, I don't care. I just want to ask, in your time of presentation technology, the Keynote of the screen is filled with your years of quiet art, which is to make what?

In addition, when you can eat face, why get cock wire Programmer jobs? Paul Frank iPad Air Case
All in all, beauty simply scored and nine Yang soymilk machine without fortification. According to Huang Yuan's introduction, the reporter brain make up two games:
Sweet: the cock into your favorite goddess of soya-bean milk machine, in the sunny morning automatically made her a cup of soy milk.
Horror: cock wire into your favorite goddess of soya-bean milk machine, wanted in sunny morning automatically made her a cup of soy milk. But goddess got up and was about to make my own soy milk, then the blade suddenly rotated, just cut my artery, blood. Goddess of death.
Apple, don't hide, be you.
Show part of the team is full of college students, the great God Pangu class iOS jailbreak team also got busy. In the demo link, team members INT80 casually clicked on start the jailbreak, iOS8.4.1 have been hacked, cracked, broken, solution,.
As the great god Pan gu, of course not showing specific vulnerabilities, but easily won the HackPwn award. (Middle school students bullying-Visual da full of kindergarten children. ) However, Pangu team announced that it would donate the bonus of 200,000 yuan in Tianjin get families of fireman killed in the accident, the News won warm applause from the audience. Asked by Lei feng's network will soon release a jailbreak tool iOS8.4.1, light INT80 fengqing said: "no, we want to keep vulnerabilities to iOS 9. "The wind of God reflected ...
Summary
Throughout the HackPwn this year, targeting mostly premature's intelligent home and Internet. Qihoo 360, President and Group CEO of qihoo 360 enterprises security, said: "in the face of sudden Internet of things era, users are not sufficient, the lack of security awareness; also unprepared without basic protection schema. "
In today's scene, hackers showed many of the vulnerabilities that can be used to make illicit profits. However, they publicly announced the vulnerability (to prevent illegal access to, and did not disclose technical details), which is also in such a high profile way to remind your hardware manufacturer: in the eyes of hackers, everything can be broken, but should not be so easily broken.
Hope those shoes down the server before starting service, have fixed the vulnerabilities.
Tips


Micro sweep sweep, author tips bar ~

1946 votes
Millet bracelet
Bracelet with millet millet's latest wearable device, with intelligent features such as alarm clock sleep monitoring.
View details of the voting >> Paul Frank iPad Air Case

No comments:
Post a Comment